In the ever-evolving digital landscape, networking has become an integral part of our daily lives. Whether you’re browsing the web, streaming your favorite shows, or accessing cloud-based applications, you’re likely relying on a complex network of interconnected devices and protocols to facilitate your online activities. At the heart of this network lies a critical component known as a proxy, which plays a crucial role in how you interact with the internet.
In this comprehensive guide, we’ll delve into the world of proxies, exploring their purpose, functionality, and the various types that exist in the networking realm. We’ll also discuss the benefits of using proxies, common use cases, and the potential risks and challenges associated with their implementation. By the end of this article, you’ll have a deeper understanding of the role of proxies in networking and how they can enhance your online experience.
Understanding the Concept of Proxies
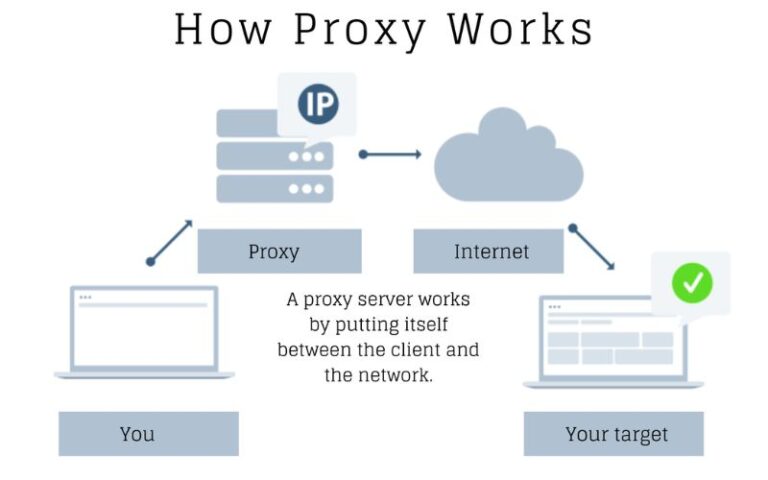
A proxy, in the context of networking, is an intermediary device or service that acts as a gateway between your device and the internet. When you request to access a website or online resource, the proxy server intercepts the request, processes it, and then forwards it to the intended destination on your behalf. This process adds an extra layer of functionality and control to your internet interactions.
Proxies serve a variety of purposes, including:
- Privacy and Security: Proxies can help protect your online privacy by masking your IP address and encrypting your internet traffic, making it more difficult for third parties to track your online activities.
- Content Filtering: Proxies can be used to restrict access to certain websites or content based on predefined policies, such as those implemented in workplace or educational environments.
- Performance Optimization: Proxies can cache frequently accessed content, reducing the load on the original server and improving the overall speed and responsiveness of your internet connection.
- Bypassing Restrictions: Proxies can be used to circumvent geographical or network-based restrictions, allowing you to access content that may be blocked in your region or network.
Understanding the fundamental concept of proxies is crucial in navigating the complexities of modern networking.
How Proxies Work in Networking
When you initiate an online request through a proxy, the process typically follows these steps:
- Client Request: Your device (the client) sends a request to the proxy server, seeking to access a specific website or online resource.
- Proxy Intercept: The proxy server receives the request and evaluates it according to its configured policies and settings.
- Request Forwarding: If the request is deemed acceptable, the proxy server forwards the request to the intended destination on the Internet.
- Response Retrieval: The proxy server receives the response from the destination server and processes it.
- Response Delivery: The proxy server then delivers the processed response back to your device, completing the transaction.
This intermediary role allows the proxy server to perform various functions, such as caching, content filtering, and IP address masking, before delivering the requested content to your device.
Types of Proxies in Networking
In the world of networking, there are several distinct types of proxies, each serving a specific purpose and offering unique features. Some of the most common types of proxies include:
- Web Proxies: These proxies are designed to handle HTTP and HTTPS traffic, allowing users to access websites and web-based applications through the proxy server.
- Transparent Proxies: Transparent proxies are designed to intercept and process network traffic without the user’s explicit knowledge or configuration, providing a seamless experience.
- Reverse Proxies: Reverse proxies are typically used on the server side to manage and distribute incoming traffic to multiple backend servers, improving performance and load balancing.
- SOCKS Proxies: SOCKS proxies operate at the network layer, providing a more versatile and protocol-agnostic proxy solution that can handle a wide range of internet traffic, including non-web protocols.
- Anonymous Proxies: These proxies are designed to mask the user’s IP address and provide an additional layer of privacy and anonymity when accessing the internet.
Understanding the different types of proxies and their unique characteristics is essential in selecting the right proxy solution for your specific networking needs.
Benefits of Using Proxies in Networking
Incorporating proxies into your networking strategy can provide a range of benefits, including:
- Enhanced Privacy and Security: Proxies can help protect your online privacy by masking your IP address and encrypting your internet traffic, making it more difficult for third parties to track your activities.
- Improved Performance: Proxy servers can cache frequently accessed content, reducing the load on the original server and improving the overall speed and responsiveness of your internet connection.
- Content Filtering and Access Control: Proxies can be used to restrict access to certain websites or content based on predefined policies, which can be useful in workplace or educational environments.
- Bypassing Restrictions: Proxies can be used to circumvent geographical or network-based restrictions, allowing you to access content that may be blocked in your region or network.
- Centralized Management: Proxy servers can provide a centralized point of control and management for your network traffic, simplifying the implementation of security policies and monitoring.
By leveraging the benefits of proxies, you can enhance your online experience, improve the security and performance of your network, and gain greater control over your internet interactions.
Common Use Cases for Proxies in Networking
Proxies have a wide range of applications in the networking landscape, catering to the diverse needs of individuals and organizations. Some of the most common use cases for proxies include:
- Corporate and Enterprise Networks: Proxies are widely used in corporate and enterprise environments to manage and secure network traffic, enforce content filtering policies, and provide centralized control over internet access.
- Educational Institutions: Schools and universities often employ proxies to restrict access to certain websites or online resources, ensuring a safe and productive learning environment for students.
- Personal Privacy and Security: Individuals can use proxies to enhance their online privacy, bypass geographical restrictions, and protect their sensitive information from potential threats.
- Content Delivery Networks (CDNs): Reverse proxies are commonly used in CDNs to distribute web content across multiple servers, improving the overall performance and availability of websites and web applications.
- Remote Access and Telecommuting: Proxies can facilitate secure remote access to corporate resources, enabling employees to work from home or other locations while maintaining the integrity of the network.
Understanding these common use cases can help you identify the most appropriate proxy solution for your specific networking requirements.
How to Set Up a Proxy in Networking
Setting up a proxy in your networking environment typically involves the following steps:
- Choose a Proxy Server: Select a reliable proxy server provider or set up your proxy server, considering factors such as performance, security, and features.
- Configure Client Devices: Depending on the type of proxy you’re using, you’ll need to configure your client devices (e.g., laptops, smartphones, or desktops) to use the proxy server. This may involve modifying browser settings, using a proxy client application, or implementing a centralized proxy configuration.
- Establish Proxy Policies: Define and implement policies that govern the use of the proxy server, such as content filtering rules, access control, and user authentication requirements.
- Monitor and Maintain the Proxy: Regularly monitor the performance and usage of the proxy server, and implement necessary updates or modifications to ensure optimal functionality and security.
The specific steps for setting up a proxy will vary depending on the type of proxy, the networking environment, and the tools and technologies you’re using. It’s recommended to consult with networking professionals or refer to the documentation provided by your proxy server provider for detailed instructions on the setup process.
Proxy Servers and Their Role in Networking
Proxy servers play a crucial role in modern networking by acting as intermediaries between client devices and the internet. These servers handle a wide range of responsibilities, including:
- Traffic Interception and Forwarding: Proxy servers receive client requests, evaluate them based on configured policies, and then forward the requests to the intended destination on the internet.
- Content Caching: Proxy servers can cache frequently accessed content, reducing the load on the original server and improving the overall speed and responsiveness of the network.
- IP Address Masking: Proxy servers can mask the client’s IP address, providing an additional layer of privacy and anonymity when accessing the internet.
- Security and Access Control: Proxy servers can enforce security policies, such as content filtering and user authentication, to protect the network and its resources.
- Load Balancing: Reverse proxy servers can distribute incoming traffic across multiple backend servers, improving the overall performance and availability of web-based applications and services.
By leveraging the capabilities of proxy servers, organizations and individuals can enhance their online experience, improve network security, and optimize the performance of their internet-based applications and services.
Risks and Challenges Associated with Proxies in Networking
While proxies offer numerous benefits, there are also some risks and challenges associated with their implementation in a networking environment. These include:
- Security Vulnerabilities: Poorly configured or maintained proxy servers can introduce security vulnerabilities, potentially exposing the network and its users to various threats, such as data breaches, malware infections, and unauthorized access.
- Performance Bottlenecks: If the proxy server is not properly sized or configured to handle the network’s traffic load, it can become a bottleneck, leading to slower response times and decreased overall performance.
- Compliance and Regulatory Concerns: Depending on the industry and applicable regulations, the use of proxies may raise compliance issues, particularly in areas related to data privacy, content monitoring, and user privacy.
- User Resistance: Some users may be hesitant to use a proxy server, perceiving it as an infringement on their online freedom or privacy, which can lead to resistance and challenges in implementing the proxy solution.
- Proxy Circumvention: Sophisticated users or malicious actors may attempt to bypass or circumvent the proxy server, rendering the security and access control measures ineffective.
To mitigate these risks and challenges, it’s crucial to carefully plan and implement your proxy solution, ensuring that it aligns with your organization’s security policies, performance requirements, and user needs.
Conclusion
In the ever-evolving world of networking, proxies have become an indispensable component, serving a wide range of purposes and providing numerous benefits to both individuals and organizations. From enhancing online privacy and security to optimizing network performance and enabling access control, proxies play a crucial role in shaping the way we interact with the internet.
As you’ve learned throughout this comprehensive guide, proxies offer a versatile and powerful solution for addressing the diverse challenges faced in modern networking environments. By understanding the concept of proxies, their various types, and the benefits they provide, you can make informed decisions and implement the right proxy solution to suit your specific needs.
To learn more about how proxies can enhance your networking experience, explore our [guide on the best proxy services](https://www.example.com/best-proxy-services) or [contact our team of networking experts](https://www.example.com/contact) for personalized recommendations and implementation support.