In the world of web applications and server infrastructure, a reverse proxy has become an essential component for many organizations. A reverse proxy is a type of proxy server that sits between the client and the origin server, acting as an intermediary and handling various tasks on behalf of the origin server. This article will delve into the intricacies of reverse proxies, exploring how they work, their benefits, common use cases, implementation scenarios, and the different types of Reverse Proxy Servers available.
Introduction to Reverse Proxy
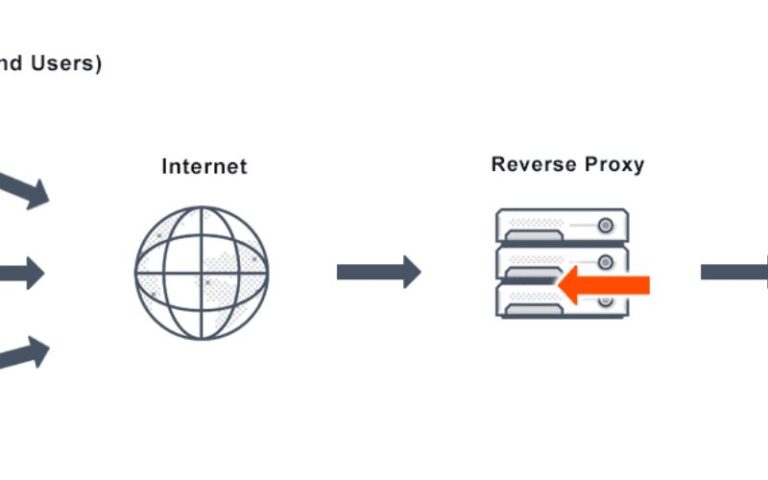
A reverse proxy is a server that sits in front of one or more web servers, intercepting requests from clients (such as web browsers) and forwarding them to the appropriate server. Unlike a forward proxy, which acts on behalf of the client, a reverse proxy operates on behalf of the web server, shielding the origin server from direct client interactions.
The primary purpose of a reverse proxy is to provide an additional layer of abstraction, security, and functionality between the client and the origin server. By handling tasks such as load balancing, caching, SSL/TLS termination, and security monitoring, a reverse proxy can enhance the performance, scalability, and overall security of a web application.
How Does a Reverse Proxy Work?
When a client makes a request to a web application, the request is first received by the reverse proxy server. The reverse proxy then analyzes the request, determines the appropriate origin server to handle the request, and forwards the request to that server. Once the origin server has processed the request and generated the response, the reverse proxy receives the response, performs any necessary transformations or optimizations, and then sends the final response back to the client.
This process can be summarized as follows:
- The client sends a request to the reverse proxy.
- The reverse proxy receives the request and analyzes it.
- The reverse proxy determines the appropriate origin server to handle the request.
- The reverse proxy forwards the request to the origin server.
- The origin server processes the request and generates the response.
- The reverse proxy receives the response from the origin server.
- The reverse proxy performs any necessary transformations or optimizations on the response.
- The reverse proxy sends the final response back to the client.
By acting as an intermediary, the reverse proxy can provide a range of benefits to both the client and the origin server, as we’ll explore in the next section.
Benefits of Using a Reverse Proxy
Implementing a reverse proxy in your web infrastructure can offer several advantages:
- Load Balancing: A reverse proxy can distribute incoming traffic across multiple origin servers, ensuring that no single server becomes overloaded and improving the overall responsiveness of the application.
- Caching: Reverse proxies can cache frequently accessed content, reducing the load on the origin servers and improving response times for clients.
- SSL/TLS Termination: Reverse proxies can handle the SSL/TLS encryption and decryption process, offloading this resource-intensive task from the origin servers.
- Security: Reverse proxies can provide an additional layer of security by filtering out malicious traffic, monitoring for potential attacks, and shielding the origin servers from direct client interactions.
- Scalability: By abstracting the client-server communication, reverse proxies make it easier to scale the infrastructure by adding or removing origin servers as needed, without the client’s knowledge.
- Centralized Configuration: Reverse proxies allow for centralized management and configuration of the web application, simplifying tasks such as SSL/TLS certificate management, URL rewriting, and access control.
- Logging and Monitoring: Reverse proxies can provide comprehensive logging and monitoring capabilities, making it easier to troubleshoot issues and analyze the usage patterns of the web application.
- Disaster Recovery: In the event of an origin server failure, a reverse proxy can seamlessly redirect traffic to a backup server, ensuring high availability and minimizing downtime.
By leveraging these benefits, organizations can improve the performance, security, and scalability of their web applications, ultimately delivering a better user experience for their clients.
Common Use Cases for Reverse Proxy
Reverse proxies can be employed in a variety of scenarios to address different needs. Some of the most common use cases include:
- Load Balancing: Distributing incoming traffic across multiple origin servers to improve responsiveness and prevent overloading any single server.
- SSL/TLS Termination: Handling the SSL/TLS encryption and decryption process, offloading this resource-intensive task from the origin servers.
- Content Caching: Caching frequently accessed static content, such as images, CSS, and JavaScript files, to reduce the load on the origin servers and improve response times.
- Security and Access Control: Filtering out malicious traffic, enforcing access control policies, and providing an additional layer of security between the clients and the origin servers.
- URL Rewriting and Routing: Rewriting and redirecting URLs to provide a more user-friendly and intuitive interface for the web application.
- Microservices Architecture: Integrating and managing the communication between multiple microservices, providing a unified entry point for clients.
- Content Delivery Network (CDN) Integration: Integrating with a CDN to serve static content from geographically distributed servers, improving global content delivery performance.
- Disaster Recovery and High Availability: Providing failover capabilities and redirecting traffic to backup servers in the event of an origin server failure.
By understanding these common use cases, you can better evaluate the potential benefits of implementing a reverse proxy in your web infrastructure and determine the most suitable scenarios for its deployment.
Implementing a Reverse Proxy in Different Scenarios
Reverse proxies can be implemented in various scenarios, depending on the specific needs of your web application. Here are a few common implementation scenarios:
- Single Origin Server: In a basic setup, a reverse proxy can be used in front of a single origin server to handle tasks such as load balancing, caching, and SSL/TLS termination.
- Multiple Origin Servers: When scaling your web application, a reverse proxy can be used to distribute traffic across multiple origin servers, providing load balancing and high availability.
- Microservices Architecture: In a microservices-based application, a reverse proxy can be used to integrate and manage the communication between multiple microservices, providing a unified entry point for clients.
- Content Delivery Network (CDN) Integration: Reverse proxies can be integrated with a CDN to serve static content from geographically distributed servers, improving global content delivery performance.
- Hybrid Cloud or Multi-Cloud Environments: Reverse proxies can be used to manage the communication between on-premises and cloud-based infrastructure, enabling seamless integration and load balancing across different environments.
- Legacy Application Integration: Reverse proxies can be used to provide a modern, user-friendly interface for legacy applications, handling tasks such as URL rewriting and security enforcement.
Regardless of the specific scenario, the implementation of a reverse proxy typically involves configuring the reverse proxy server, defining the routing rules, setting up load balancing and caching policies, and integrating the reverse proxy with the origin servers or other components of the web infrastructure.
Types of Reverse Proxy Servers
There are several types of reverse proxy servers available, each with its own set of features and capabilities. Some of the most common types include:
- Web Server-Based Reverse Proxies: These are reverse proxy functionalities built into popular web servers, such as Apache HTTP Server (with mod_proxy) or Nginx.
- Standalone Reverse Proxy Servers: Dedicated reverse proxy software like Nginx, HAProxy, or Traefik, which are designed specifically for the purpose of reverse proxying.
- Cloud-Based Reverse Proxies: Reverse proxy services offered by cloud providers, such as Amazon Web Services’ (AWS) Application Load Balancer or Google Cloud’s Cloud Load Balancing.
- Content Delivery Network (CDN)-Integrated Reverse Proxies: Reverse proxy functionalities provided by CDN providers, which can handle tasks like caching, SSL/TLS termination, and global load balancing.
- Reverse Proxy Gateways: Reverse proxies that also provide additional functionality, such as API management, authentication, or service mesh integration, like Kong or Istio.
When choosing a reverse proxy solution, consider factors such as performance, scalability, feature set, ease of use, and integration with your existing web infrastructure and toolchain. The specific requirements of your web application will help you determine the most suitable type of reverse proxy server.
Security Considerations and Best Practices for Reverse Proxy
While reverse proxies offer numerous benefits, it’s essential to address the security implications and implement best practices to ensure the overall security of your web infrastructure. Some key considerations and best practices include:
- SSL/TLS Termination: Ensure that the SSL/TLS termination process is properly configured and that the reverse proxy is using the latest and most secure encryption protocols.
- Access Control and Authentication: Implement robust access control policies and authentication mechanisms to prevent unauthorized access to the origin servers.
- Web Application Firewall (WAF): Integrate a web application firewall with the reverse proxy to detect and mitigate common web application attacks, such as SQL injection and cross-site scripting (XSS).
- Logging and Monitoring: Establish comprehensive logging and monitoring mechanisms to track and analyze the activities and potential security incidents related to the reverse proxy.
- Regular Updates and Patches: Keep the reverse proxy software and its dependencies up-to-date with the latest security patches and updates to address known vulnerabilities.
- Network Segmentation: Separate the reverse proxy server from the origin servers and other critical infrastructure components to limit the potential impact of a breach.
- Secure Communication: Ensure that the communication between the reverse proxy and the origin servers is secure, using techniques like mutual TLS authentication.
- Secure Configuration: Properly configure the reverse proxy server, following the vendor’s best practices and security recommendations to minimize the attack surface.
- Incident Response and Disaster Recovery: Develop a comprehensive incident response plan and disaster recovery strategy to ensure the resilience of the web infrastructure in the event of a security breach or system failure.
By addressing these security considerations and implementing best practices, you can enhance the overall security of your web application and mitigate the risks associated with the use of a reverse proxy.
Key Differences Between Reverse Proxy and Load Balancer
While reverse proxies and load balancers are often used in conjunction, there are some key differences between the two:
- Purpose:
- Reverse Proxy: A reverse proxy acts as an intermediary between clients and the origin servers, handling tasks such as security, caching, and SSL/TLS termination.
- Load Balancer: A load balancer distributes incoming traffic across multiple servers to improve performance and availability.
- Directionality:
- Reverse Proxy: A reverse proxy receives requests from clients and forwards them to the appropriate origin server.
- Load Balancer: A load balancer receives requests from clients and distributes them across multiple servers.
- Functionality:
- Reverse Proxy: Reverse proxies can provide additional functionality, such as URL rewriting, content caching, and security monitoring.
- Load Balancer: Load balancers primarily focus on distributing traffic and ensuring high availability.
- Deployment:
- Reverse Proxy: Reverse proxies are typically deployed in front of the origin servers.
- Load Balancer: Load balancers can be deployed in front of the origin servers or between the reverse proxy and the origin servers.
In many cases, reverse proxies and load balancers are used together to provide a comprehensive solution, with the reverse proxy handling the additional functionality and the load balancer managing the distribution of traffic across the origin servers.
Popular Reverse Proxy Software and Tools
There are several popular reverse proxy software and tools available, each with its own set of features and capabilities. Some of the most widely used options include:
- Nginx: A high-performance web server and reverse proxy, known for its efficiency and scalability.
- HAProxy: A powerful and versatile load balancer and reverse proxy, often used in high-traffic environments.
- Traefik: A modern, cloud-native reverse proxy and load balancer, designed to be easy to use and integrate with various platforms and services.
- Apache HTTP Server: The popular Apache web server, which can also be configured to act as a reverse proxy using the mod_proxy module.
- Varnish Cache: A high-performance HTTP reverse proxy and content cache, often used to improve the performance of web applications.
- Squid: A widely-used open-source proxy server that can be configured to act as a reverse proxy.
- Envoy Proxy: A high-performance, open-source proxy developed by Lyft, often used in service mesh and microservices architectures.
- NGINX Plus: The commercial version of Nginx, which offers additional features and support for enterprise-grade deployments.
When selecting a reverse proxy solution, consider factors such as performance, scalability, feature set, ease of use, and integration with your existing web infrastructure and toolchain. The specific requirements of your web application will help you determine the most suitable reverse proxy software or tool.
Conclusion
In the world of web applications and server infrastructure, reverse proxies have become an essential component for many organizations. By acting as an intermediary between clients and origin servers, reverse proxies can provide a range of benefits, including load balancing, caching, SSL/TLS termination, and enhanced security.
As you’ve learned in this article, reverse proxies can be implemented in various scenarios, from single origin servers to complex microservices architectures and hybrid cloud environments. Understanding the different types of reverse proxy servers and the key considerations for their implementation, including security best practices, is crucial for ensuring the optimal performance, scalability, and security of your web application.
To learn more about how a reverse proxy can benefit your web application, consider speaking with one of our experts. They can help you evaluate your specific needs and recommend the most suitable reverse proxy solution for your infrastructure. [Contact us today](https://example.com/contact) to schedule a consultation.